· Zen HuiFer · Building an Enterprise-level IoT Platform from Scratch · 需要27 分钟阅读
Basic Knowledge of IoT
This chapter summarizes the basic knowledge of IoT, including network communication, data collection, data storage and management, device management and maintenance, data analysis and intelligent decision-making, edge computing and IoT, etc. Through these contents, readers can fully understand the basic concepts and application scenarios of IoT.

Basic Knowledge
Network Communication
Network communication is the foundation of information transmission between devices in the Internet of Things (IoT). In the digital age, whether it is short-distance smart home devices or industrial monitoring systems spanning continents, they all rely on a complex network communication mechanism to achieve data exchange.
Network Communication - Basic Concepts
The basic concepts of network communication include data packets, signals, transmission media, and network protocols. First, let’s explain data packets. A data packet is the basic unit of data transmission in network communication. A data packet may contain the following contents:
Header: Contains control information, such as source address, destination address, transmission protocol type, etc. The header may also contain additional information, such as segmentation information (for TCP), error detection and correction codes, packet sequence numbers, etc.
Payload/Data: This is the actual data part transmitted in the data packet. It can be any form of data, such as file content, messages, instructions, etc.
Trailer: In some protocols, the trailer may contain additional error detection information, such as cyclic redundancy check (CRC) or other checksum algorithms to ensure data integrity.
Start Bit: At the physical layer, the start of a data packet may be identified by a specific start bit pattern to notify the receiving device of the start of data transmission.
End Bit: Corresponding to the start bit, the end bit indicates the end of the data packet. In some communication protocols, the end bit may be followed by checksum information.
Synchronization Bits: In some data link layer protocols, synchronization bits are used to ensure clock synchronization between the sender and receiver.
Padding: If the data part does not fill the entire data packet, padding bits may be needed to ensure that the data packet meets the minimum length requirement or alignment requirement.
Next, let’s explain signals. In communication systems, a signal is a physical waveform or electromagnetic wave that carries information. It can vary over time and propagate in space. Signals can be electrical, optical, mechanical, or any other form of energy change used to represent data or information. Generally, signals are divided into two categories: analog signals and digital signals.
- Analog Signal
- Analog signals are continuously varying waveforms that can simulate physical quantities in the real world, such as sound, temperature, or light intensity.
- They are continuous in time and amplitude and can change infinitely.
- Common transmission media for analog signals include copper wires, radio waves, etc.
- Digital Signal
- Digital signals consist of discrete values, usually in binary form, i.e., 0 and 1.
- They represent information in a discrete manner, using electronic or optical switches to indicate state changes.
- Digital signals are easy to process by computers and other digital devices, have high resistance to interference, and are easy to store.
Next, let’s explain transmission media. In communication systems, transmission media are the physical carriers for signal propagation. Common transmission media include:
- Twisted Pair: Consists of two insulated copper wires, commonly used in Ethernet.
- Fiber Optic: Uses light signals to transmit data, with high bandwidth and long-distance transmission capabilities.
- Wireless: Transmits signals through the air, enabling wireless communication.
Finally, let’s explain network protocols. Network protocols define the rules and standards for data transmission between electronic devices. They cover various levels from electrical specifications of physical hardware to advanced data processing, ensuring that data can be effectively and reliably transmitted between different devices and networks. The OSI model and TCP/IP model are two widely accepted network communication models that specify how data is encapsulated, addressed, transmitted, and decapsulated in the network. The OSI model is a seven-layer model, while the TCP/IP model is usually considered a four-layer or five-layer model. The implementation of network protocols includes both software and hardware aspects, involving network stacks in operating systems and hardware devices such as network interface cards.
Network Communication - Network Topology
In the field of network communication, Network Topology defines how devices (nodes) are connected and arranged through transmission media (links). Choosing the right network topology is crucial for ensuring the performance, reliability, and scalability of the network. Common network topologies are as follows.
- Star Topology: Star topology is the most common network layout, where all nodes are directly connected to a central node (usually a switch or hub). This topology is easy to install and manage, supports plug-and-play, but a failure of the central node can lead to the entire network being paralyzed.
- Ring Topology: In a ring topology, each node is connected to two adjacent nodes through two links, forming a closed loop. This design ensures sequential data transmission in the ring, reducing collisions, but any failure in the loop can affect the entire network.
- Bus Topology: In a bus topology, all nodes are connected to a shared communication medium (bus). This topology is cost-effective and easy to install, but damage to the bus can lead to network interruptions and it is difficult to locate faults.
- Mesh Topology: Mesh topology provides multiple connection paths between multiple nodes. This topology has high redundancy and reliability, but it is costly and becomes more complex to manage as the number of nodes increases.
- Tree Topology: Tree topology is a combination of star and bus topologies, forming a hierarchical tree structure. It is suitable for large networks, providing good scalability, but a failure in the trunk can affect the entire network.
- Hybrid Topology: Hybrid topology combines two or more topologies to meet specific network needs. This topology provides flexibility and scalability, but design and management can be more complex.
| Topology Name | Advantages | Disadvantages |
|---|---|---|
| Bus | - Cable cost is very low. - Cheap and easy to install. - Widely applicable to small, simple, or temporary networks. | - If a device on the link fails, the entire system will crash. - When network traffic is high, it is easy to cause conflicts in the network. - The length of the cable is always limited, which is not conducive to expansion. |
| Ring | - Easy to install and reconfigure. - Adding or removing devices in the ring topology only requires moving two connections. - All computers have equal access. - Faster error checking and confirmation. | - Unidirectional traffic. - A single ring interruption may cause the entire network to be interrupted. - Troubleshooting is very difficult. - Adding or removing computers may interfere with network activity. |
| Star | - Easy to troubleshoot, set up, and modify. - If some nodes fail, other nodes can still work normally. - Fast performance, few nodes, and very low network traffic. - Easy to add, remove, and move devices. | - If the hub or concentrator fails, the connected nodes will be disabled. - High installation cost. - Busy network traffic sometimes significantly reduces bus speed. - Performance depends on the capacity of the hub. |
| Mesh | - The network can be expanded without interrupting current users. - No traffic problems. - Mesh topology is robust. - Multiple links, data communication is not limited to a single path. - Fault identification and isolation process is easy. | - Complex installation. - Expensive, using more cables. - Complex implementation. - Requires more space for dedicated links. - High implementation cost. |
| Tree | - Failure of one node does not affect the rest of the network. - Node expansion is quick and easy. - Easy error detection. - Easy to manage and maintain. | - Wiring intensive. - Maintenance is difficult if more nodes are added. - If the hub or concentrator fails, the connected nodes will also be disabled. |
| Hybrid | - Provides the simplest error detection and troubleshooting methods. - Efficient and flexible network topology. - Scalable. | - Complex structural design. - Highest cost. |
Network Communication - Signal Transmission Methods
In network communication, the signal transmission method determines how data moves between devices in the network. There are two main signal transmission methods: analog transmission and digital transmission, each with its unique characteristics and application scenarios.
- Analog Transmission: Analog transmission uses continuously varying signals to represent information. This transmission method can simulate physical quantities in the real world, such as changes in the intensity of sound or light.
- Digital Transmission: Digital transmission represents information through discrete values, usually in binary form, i.e., 0 and 1.
The comparison information between analog transmission and digital transmission is shown in the table.
| Characteristics/Transmission Method | Analog Transmission | Digital Transmission |
|---|---|---|
| Signal Representation | Continuously varying waveforms | Discrete binary values (0 and 1) |
| Signal Type | Continuous signal | Discrete signal |
| Anti-interference Ability | Weak, easily affected by noise | Strong, with error detection and correction capabilities |
| Transmission Medium | Copper wire, radio waves, etc. | Copper wire, fiber optic, radio waves, etc. |
| Long-distance Transmission | Requires signal amplifiers or repeaters | Usually more suitable for long-distance transmission |
| Bandwidth Utilization | Usually low | More efficient, supports higher-speed data transmission |
| Signal Attenuation | Easily attenuated over long distances | Can reduce attenuation effects through signal regeneration |
| Modulation/Encoding Requirements | Usually requires modulation | Requires encoding and modulation |
| Error Handling | Difficult to detect and correct errors | Supports error detection and correction mechanisms |
| Application Examples | Traditional telephone lines, radio broadcasting | Internet, mobile phones, digital television |
| Compatibility | Directly simulates real-world signals | Requires digital-to-analog conversion devices (such as modems) |
Network Communication - Communication Medium
In network communication, the communication medium is the physical basis for transmitting signals, determining the way and characteristics of data transmission. Communication media are divided into wired communication media and wireless communication media. The specific comparison can be referred to in the following two tables.
| Characteristics/Medium Type | Twisted Pair | Coaxial Cable | Fiber Optic |
|---|---|---|---|
| Material | Copper or aluminum conductor | Copper central conductor and shield | Glass or plastic fiber |
| Transmission Method | Electrical signal | Electrical signal | Optical signal |
| Bandwidth | Low to medium | Medium | Very high |
| Transmission Rate | 10Mbps to 1Gbps | 250Mbps to 10Gbps | 100Mbps to 100Gbps and above |
| Transmission Distance | Short to medium | Medium | Long distance |
| Anti-interference Ability | Poor, easily affected by electromagnetic interference | Good | Excellent, not affected by electromagnetic interference |
| Installation Difficulty | Low | Medium | High |
| Cost | Low | Medium | High |
| Application Scenarios | Telephone lines, LANs | Cable TV, some LANs | High-speed networks, data centers, long-distance communication |
| Resistance | Easily affected by the environment | Certain resistance to environmental impact | Corrosion-resistant, moisture-resistant, electromagnetic-resistant |
| Signal Attenuation | Yes, attenuation increases with distance | Low attenuation | Almost no attenuation |
| Characteristics/Medium Type | Radio Waves | Microwaves | Infrared |
|---|---|---|---|
| Material | No physical medium, transmitted through air | No physical medium, transmitted through air | No physical medium, transmitted through air |
| Transmission Method | Electromagnetic waves | Electromagnetic waves | Electromagnetic waves |
| Frequency Range | Very low frequency to ultra-high frequency | Very high frequency | Near-infrared region |
| Transmission Rate | From low to high speed | High speed | Low speed |
| Transmission Distance | Variable, depending on frequency and power | Usually line-of-sight transmission, long distance | Short distance |
| Anti-interference Ability | Easily affected by other signals and physical obstacles | Easily affected by weather conditions, but resistant to physical obstacles | Easily affected by light and obstacles |
| Installation Difficulty | Low, equipment is usually easy to deploy | Medium, requires line-of-sight path | Low, but requires alignment of equipment |
| Cost | Low to medium, depending on coverage | Medium to high, requires high-power transmitters | Low, commonly used for short-distance communication |
| Application Scenarios | Wireless networks, broadcasting, mobile communication | Point-to-point communication, satellite communication | Remote controls, short-distance data transmission |
| Security | Low, easily eavesdropped | Medium, requires line-of-sight path | Low, easily blocked by physical obstacles |
| Signal Attenuation | Affected by distance and physical obstacles | Affected by weather, but low attenuation | Affected by distance and obstacles, high attenuation |
Network Communication - Protocols
Network communication protocols define the way data is transmitted in the network, ensuring effective communication between different devices and systems. Common protocols in the field of IoT include TCP/IP, HTTP, WebSocket, COAP, MQTT, and Modbus protocols. The content of these protocols will be introduced in subsequent chapters. Here is just a basic comparison, detailed content can be seen in the table.
| Characteristics/Protocol | TCP/IP | HTTP | WebSocket | COAP | MQTT | Modbus |
|---|---|---|---|---|---|---|
| Basic Protocol Set | Yes | No | No | No | No | No |
| Communication Mode | Connection-oriented | Stateless request/response | Full-duplex communication | Request/response | Publish/subscribe | Client/server |
| Transport Layer Protocol | TCP/UDP | TCP | TCP | UDP | TCP/UDP | TCP/RTU |
| Application Layer Protocol | IP | HTTP/HTTPS | WebSocket | CoAP | MQTT | Modbus TCP/Modbus RTU |
| Data Format | Binary/Text | Text | Binary/Text | Binary | Binary | Binary |
| Header Overhead | None | Yes (HTTP header) | None after initial handshake | Small | Small | Small |
| Application Scenarios | General | Web data transmission | Real-time communication | Low-power IoT | IoT real-time messaging | Industrial automation |
| Security | Requires separate encryption | Supports HTTPS | Can be encrypted | Supports DTLS | Supports TLS | Can be encrypted |
| Supported Devices | Wide | Mainly browsers/servers | Modern browsers/servers | IoT devices | IoT devices | Industrial devices |
| Protocol Efficiency | High | High (large header overhead) | High | High | High | High (industrial environment) |
TCP/IP Protocol
Transmission Control Protocol/Internet Protocol (TCP/IP), this name may sound technical, but it is the invisible bond that connects billions of devices and users worldwide.
This set of protocols was initiated by the Defense Advanced Research Projects Agency (DARPA) of the United States in the 1970s, originally aimed at achieving interoperability and survivability of military networks. However, over time, TCP/IP has gradually evolved into the universal language of global internet communication.
The core of the TCP/IP protocol lies in its layered model, which breaks down the complex communication process into several simple sub-tasks, each executed by a specific network layer. This layered approach not only simplifies network design but also enhances network flexibility and scalability.
From the rich variety of network services at the application layer to reliable data transmission at the transport layer, intelligent routing at the network layer, and actual signal transmission at the physical layer, each layer plays an indispensable role. This layered structure, like the foundation and floors of a building, ensures the stability and efficiency of the internet.
With continuous technological advancements, the TCP/IP protocol is also evolving to meet new network demands and challenges. From the initial IPv4 to the current IPv6, from simple data transmission to complex application interactions, the TCP/IP protocol has always been driving internet innovation and development.
Next, let’s delve into the structure of the TCP/IP model. The model is divided into 5 layers, each bearing different functions and responsibilities. From top to bottom, these layers are:
- Application Layer
- Located at the top of the TCP/IP model, the application layer handles specific application details. This includes protocols we use daily, such as HTTP (web browsing), FTP (file transfer), SMTP (email sending), etc. The application layer’s functions are equivalent to the top three layers (application layer, presentation layer, session layer) of the OSI model.
- Transport Layer
- The transport layer is the bridge between the application layer and the network layer, mainly responsible for providing inter-process communication services. The two main protocols working at this layer are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). TCP provides reliable, connection-oriented communication services, while UDP offers stateless, potentially unreliable communication services.
- Internet Layer
- The core function of the internet layer is to handle the transmission and routing of data packets from source to destination. The IP protocol (Internet Protocol) is the main protocol at this layer, responsible for transmitting data packets through router networks to their destinations. Additionally, ICMP (Internet Control Message Protocol) and ARP (Address Resolution Protocol) also play roles in the internet layer.
- Data Link Layer
- The data link layer is responsible for transmitting frames between adjacent network devices. It includes error detection and correction mechanisms to ensure reliable data transmission over the physical medium. Data link layer protocols are usually related to specific network technologies (such as Ethernet).
- Physical Layer
- The physical layer is the bottom layer of the TCP/IP model, responsible for transmitting raw bit streams through physical media (such as twisted pair, optical fiber, radio waves, etc.). This layer defines the electrical, optical, or wireless signal transmission methods and physical characteristics.
TCP/IP Protocol Stack Diagram
TCP/IP protocol stack diagram
HTTP Protocol
HTTP is an application layer protocol proposed by Tim Berners-Lee in 1989, originally intended for the transmission and display of web pages. With the rapid development of the World Wide Web, HTTP has gradually become one of the most widely used protocols on the Internet.
The core of HTTP lies in its request-response model, which allows clients (such as browsers) to send requests to servers and receive responses from servers. This model not only simplifies the process of accessing web pages but also improves the efficiency of network communication.
From the URL input in the browser, to the resource processing by the server, to the rendering and display of the web page, the HTTP protocol runs through the entire process of web page access. The design of this protocol, like traffic signals, ensures the orderly and efficient flow of data.
With the development of Internet technology, HTTP is also continuously evolving. From HTTP/1.0 to HTTP/2, and to the latest HTTP/3, each update aims to improve the performance and security of network communication.
The main features of the HTTP protocol include:
- Statelessness
- The HTTP protocol itself does not maintain any connection state. Each request is independent, and the server does not save information from previous requests.
- Media Types
- HTTP allows the transmission of various types of data, such as text, images, videos, etc. Each type of data has a corresponding media type (MIME type).
- Persistent Connections
- Persistent connections were introduced in HTTP/1.1, allowing multiple requests and responses to be sent over a single TCP connection, reducing the overhead of establishing and closing connections.
- Security
- Through HTTPS (HTTP over SSL/TLS), the HTTP protocol can provide encrypted communication, protecting the security of data transmission.
- Caching
- HTTP supports caching mechanisms, allowing browsers to store accessed resources, reducing duplicate requests, and improving access speed.
- HTTP request and response flowchart
WebSocket Protocol
WebSocket, this name may not be as well-known as HTTP, but it is a key technology for modern web applications to achieve real-time communication.
This technology was standardized by the IETF (Internet Engineering Task Force) in 2011 to overcome the limitations of the traditional HTTP protocol in real-time communication. WebSocket provides a full-duplex communication channel, allowing the server to actively send information to the client, which is crucial in scenarios such as chat applications, real-time games, and stock trading platforms.
The core of WebSocket lies in its persistent connection model, which allows bidirectional data transmission over a single TCP connection. This model not only reduces the overhead of HTTP requests and responses but also improves the efficiency of data transmission.
From the establishment of the connection by the client, to the message push by the server, to the instant response by the client, the WebSocket protocol runs through the entire process of real-time communication. The design of this protocol, like a highway, ensures the fast and continuous flow of information.
As web applications continue to evolve, WebSocket is also constantly developing to adapt to new application scenarios and user needs. From simple text message transmission to complex binary data exchange, the WebSocket protocol has always been driving the innovation and development of web communication.
The main features of the WebSocket protocol include:
- Full-Duplex Communication
- WebSocket provides a full-duplex communication channel, allowing the client and server to send and receive data simultaneously.
- Persistent Connection
- Once the WebSocket connection is established, it will remain open until the client or server explicitly closes the connection.
- Low Latency
- By avoiding the overhead of HTTP requests and responses, WebSocket can provide a near real-time communication experience.
- Protocol Upgrade
- WebSocket performs a handshake through an HTTP request, and once the handshake is successful, the communication protocol is upgraded from HTTP to WebSocket.
- Message Framing
- WebSocket defines the frame structure of messages, supports the transmission of text and binary data, and can handle large messages.
- WebSocket communication flowchart
CoAP Protocol
Constrained Application Protocol (CoAP) is a communication protocol designed specifically for the Internet of Things (IoT), known for its lightweight and efficiency.
The CoAP protocol runs on the UDP protocol and is designed to be very small, with the smallest data packet being only 4 bytes. It uses a client/server model similar to HTTP and uses a request/response mechanism for interaction. The CoAP protocol supports RESTful style APIs, allowing devices to identify and access resources through URIs, and use methods such as GET, POST, PUT, and DELETE to manipulate resources.
A notable feature of the CoAP protocol is that it supports two message transmission modes: Confirmable and Non-confirmable, to suit different application scenarios. In addition, CoAP provides an observation mode that allows observers to subscribe and receive notifications of state changes of entities, similar to the subscription function in the MQTT protocol.
The CoAP protocol is widely used in IoT, suitable for various scenarios such as smart homes, industrial automation, and environmental monitoring. It is particularly suitable for resource-constrained devices, such as low-power sensors and embedded systems. The lightweight and low-power design of the CoAP protocol makes it especially useful for battery-powered devices.
With the continuous development of IoT technology, the CoAP protocol also faces new challenges and opportunities. In the future, the CoAP protocol may see further development and enhancement in standardization, security, edge computing integration, and large-scale deployment.
- CoAP communication flowchart
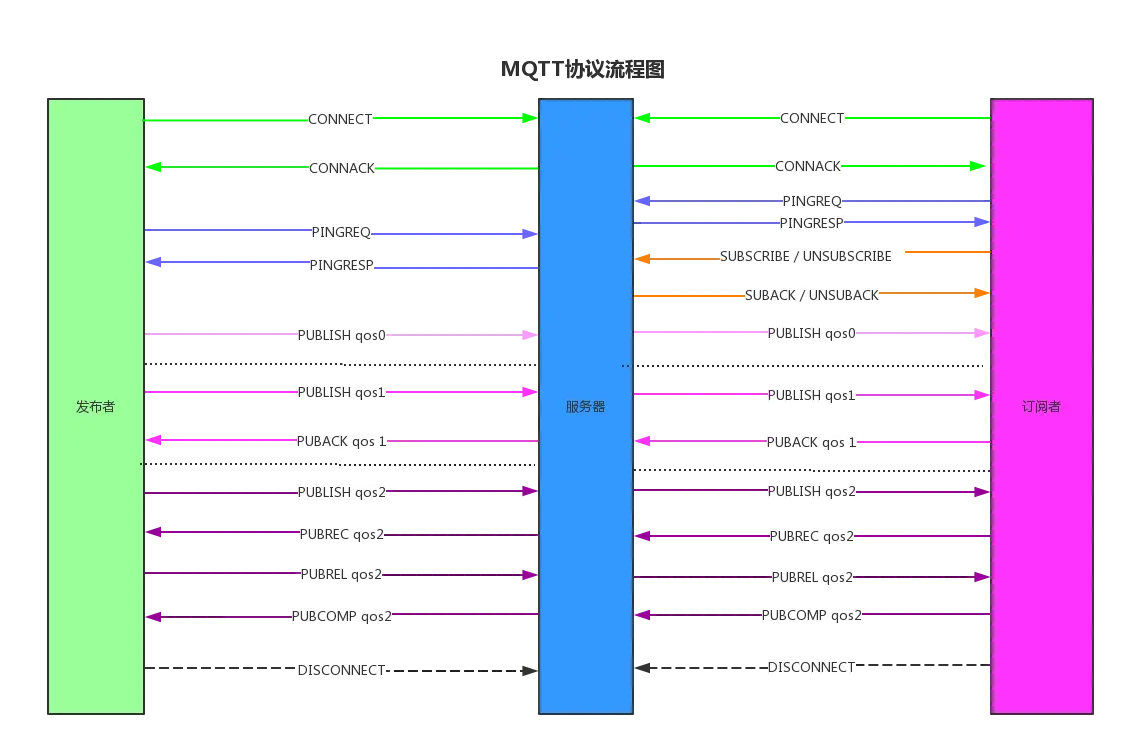
MQTT Protocol
Message Queuing Telemetry Transport (MQTT), this name may not be as long-standing as TCP/IP, but it is the main force of Internet of Things (IoT) communication.
The MQTT protocol was developed by Andy Stanford-Clark and Arun Gupta in 1999, originally aimed at optimizing the transmission of sensor data from remote oil fields. With the rise of IoT, MQTT has gradually evolved into a universal language for lightweight message communication between devices.
The essence of the MQTT protocol lies in its publish/subscribe model, which allows devices to publish messages to specific topics while other devices subscribe to these topics to receive messages. This model not only simplifies the message distribution process but also improves communication efficiency and reliability.
From real-time data reporting on the device side, to command issuance on the cloud side, and to the response of other devices, the MQTT protocol runs through the entire communication process of the Internet of Things. The design of this protocol, like an efficient logistics system, ensures the orderly and rapid flow of information.
With the continuous advancement of IoT technology, the MQTT protocol is also constantly evolving to meet new communication needs and challenges. From QoS (Quality of Service) level 0 to level 2, the MQTT protocol provides different levels of message delivery guarantees to meet the needs of different scenarios, from fire alarm sensors to environmental monitoring.
In-depth understanding of the structure of the MQTT model, we can find its core components:
Client
- The client is the sender or receiver of messages in the MQTT system. It can be a sensor, a smartphone, or any other device that can connect to the MQTT broker.
Topic
- The topic is the classification label of MQTT messages, similar to the path of a file system. Clients can subscribe to or publish messages to specific topics.
Broker
- The broker is the message center of the MQTT system, responsible for receiving, storing, and forwarding messages. It acts as a bridge for communication between clients.
Quality of Service (QoS)
- MQTT defines three different QoS levels to ensure different levels of message delivery guarantees according to application needs:
- QoS 0: At most once, the message may be lost.
- QoS 1: At least once, ensuring the message is delivered at least once.
- QoS 2: Exactly once, ensuring the message is delivered only once.
- MQTT defines three different QoS levels to ensure different levels of message delivery guarantees according to application needs:
Retained Message
- The retained message is the last message stored on the broker. When a new subscriber subscribes to the topic, it will receive this message even if the message has already been published.
Last Will and Testament
- The last will and testament is a message registered by the client when connecting to the broker. If the client disconnects abnormally, the broker will publish this message to the topic subscribed by the client.
- MQTT communication flowchart
Modbus Protocol
Modbus Protocol, this is a communication protocol widely used in the field of industrial automation, favored for its simplicity and reliability.
The Modbus protocol was originally developed by Modicon (now Schneider Electric) in 1979, with the initial purpose of achieving data exchange between industrial devices. With the development of industrial automation technology, Modbus has become one of the most common protocols in the field of industrial control.
The design concept of the Modbus protocol is simple and efficient. It is based on a client-server model, allowing multiple client devices to communicate with one or more server devices. This model not only simplifies the design of industrial networks but also improves the flexibility and scalability of the system.
From data reading of programmable logic controllers (PLCs) to control of remote input/output (I/O) devices, the Modbus protocol runs through the entire communication process of industrial automation. The design of this protocol, like the nervous system of industrial equipment, ensures the orderly and efficient flow of information between devices.
With the continuous advancement of automation technology, the Modbus protocol is also constantly evolving to meet new industrial needs and challenges. The Modbus protocol supports multiple transmission methods, including RTU (binary mode), ASCII (text mode), and TCP/IP (network-based communication).
Next, an in-depth understanding of the structure and characteristics of the Modbus protocol:
- Application Layer
- The Modbus protocol mainly operates at the application layer, responsible for achieving communication and data exchange between devices.
- Data Unit
- The Modbus protocol executes specific operations through data units such as function codes, data addresses, and registers, such as reading or writing register values.
- Transmission Mode
- Modbus supports multiple transmission modes, including RTU mode (using binary data packets), ASCII mode (using plaintext data packets), and TCP mode (using the TCP/IP protocol stack).
- Network Layer
- In Modbus communication based on TCP/IP, the Modbus protocol uses TCP as the transport layer protocol to achieve reliable communication between devices.
- Data Link and Physical Layers
- The Modbus protocol defines electrical characteristics, signal rates, connector types, etc., at these layers to adapt to different industrial network environments.
- Function Codes
- The Modbus protocol defines multiple function codes for performing different operations, such as reading (0x03), writing (0x06), and reading/writing multiple registers (0x17).
Security Basics
With the rapid development of Internet of Things (IoT) technology, our world is becoming smarter and more connected. From home automation to industrial systems, smart devices are gradually becoming an indispensable part of our daily lives and productivity. This connectivity also comes with new security challenges. These challenges, though complex, are not insurmountable. Common security challenges and solutions are shown in the table.
| Challenge Name | Challenge Description | Solution Overview |
|---|---|---|
| Device Security Vulnerabilities | Many IoT devices have known vulnerabilities at the factory, making them easy targets for hackers. | Implement secure design principles, conduct thorough security testing, and provide timely firmware updates. |
| Untimely Firmware Updates | Devices lack automated update mechanisms, leading to long-term unpatched security vulnerabilities. | Establish automated update systems and educate users to keep systems up to date. |
| Weak Authentication Mechanisms | Using weak passwords or no authentication measures makes devices vulnerable to unauthorized access. | Adopt multi-factor authentication and enforce strong password policies. |
| Insufficient Data Encryption | Data is not encrypted during transmission and storage, making it susceptible to leakage or tampering. | Use strong encryption standards to protect data and implement end-to-end encryption. |
| Insufficient Privacy Protection | Personal and sensitive information is not adequately protected after collection, increasing the risk of privacy breaches. | Implement privacy protection measures such as data minimization and anonymization. |
| Botnet Threats | Insecure devices may be recruited into botnets to launch large-scale cyber attacks. | Strengthen network monitoring to detect and isolate devices with abnormal behavior in a timely manner. |
| Supply Chain Security Risks | Security vulnerabilities may be implanted during the production or distribution of devices. | Enhance supply chain security management and implement vendor security assessments. |
| Identity and Trust Management Challenges | As the number of devices increases, managing and verifying the identity of each device becomes complex. | Adopt device identity management solutions such as blockchain technology. |
| Lagging Regulations and Standards | Security regulations and standards fail to keep up with technological developments, leading to a lack of security measures. | Actively participate in the formulation and updating of security standards to ensure regulations keep pace with technological developments. |
| Cross-Domain Communication Security Issues | Communication between different devices and systems may pose risks due to inconsistent security protocols. | Develop unified security communication standards to ensure compatibility and security of cross-platform devices. |
| Physical Security Threats | Devices may face physical damage or tampering, especially in critical infrastructure. | Implement physical security measures such as device hardening and access control. |
| Lifecycle Security Management | The entire lifecycle of a device, from production to disposal, requires security management but is often overlooked. | Develop comprehensive device management strategies, including secure decommissioning and destruction processes. |
| Insufficient User Security Awareness | Users may lack necessary security awareness and fail to take appropriate precautions. | Conduct security education and awareness campaigns to improve users’ understanding of IoT security. |
Interoperability of Devices and Platforms
In the colorful world of the Internet of Things (IoT), the interoperability of devices and platforms plays a crucial role. It determines whether devices from different manufacturers and platforms developed by different providers can work together seamlessly to build an intelligent ecosystem.
The concept of interoperability refers to the ability of different systems and components to work together, share information, and complete tasks together. In the context of IoT, this means that smart devices can break the boundaries of brands and platforms to achieve seamless data and command communication.
This interoperability brings many benefits to users, businesses, and the entire industry:
- Enhanced User Experience: Users can seamlessly use devices of different brands and types, enjoying a consistent interaction experience.
- Market Expansion: Device manufacturers and platform providers can reach a wider customer base.
- Innovation Promotion: Developers can freely integrate and innovate in an open environment, driving the development of new technologies and applications.
- Cost Efficiency: Businesses and consumers can avoid vendor lock-in and reduce costs associated with system or device replacement.
- Flexibility and Scalability: Systems can flexibly add new devices and services to meet changing business needs.
- Data Sharing: Different devices and platforms can share data, providing more comprehensive insights and decision support.
To achieve this interoperability, we can take the following specific measures:
- Standardized Protocols: Adopt standardized communication protocols (such as MQTT, CoAP, AMQP) to ensure compatibility between different systems.
- Open APIs: Provide open application programming interfaces (APIs) to allow third-party developers to access and integrate platform services.
- Middleware Usage: Use middleware to abstract the communication details of different devices and services, providing a unified interface.
- Unified Data Formats: Adopt common data formats (such as JSON, XML) to simplify data exchange between different systems.
- Security Framework: Implement a unified security framework, including authentication, authorization, data encryption, and security auditing.
- Device Directory Service: Maintain a device directory service that records metadata and capabilities of devices to facilitate service discovery and integration.
- Platform Neutrality: Design platforms to avoid dependence on specific devices or technologies, ensuring platform neutrality.
IoT Data Formats
In the world of the Internet of Things (IoT), data is the key link between the physical world and the digital world. IoT devices generate a large amount of data, and the types are diverse, so choosing the right data format is crucial for data exchange, storage, and analysis. Common data formats are as follows.
- JSON (JavaScript Object Notation) - A lightweight data interchange format that is easy for humans to read and write, and easy for machines to parse and generate.
- XML (eXtensible Markup Language) - A markup language used to store and transmit data, self-descriptive, but more complex than JSON.
- CSV (Comma-Separated Values) - A simple file format used to store tabular data, usually using commas to separate values.
- Protobuf (Protocol Buffers) - A binary serialization format developed by Google for serializing data structures.
- Avro - Part of the Apache Hadoop project, a data serialization framework that supports rich data types.
- Thrift - A cross-language service development framework developed by Facebook for data serialization.
- BSON (Binary JSON) - A binary form of JSON used by MongoDB for data storage and exchange.
- YAML (YAML Ain’t Markup Language) - A human-readable data serialization standard commonly used for configuration files.
- MessagePack - An efficient binary serialization format, similar to JSON but smaller and faster.
- CBOR (Concise Binary Object Representation) - A binary data format for data exchange, designed to be more compact than JSON.
The comparison information of the above data formats is shown in the table
| Data Format | Advantages | Disadvantages |
|---|---|---|
| JSON | - Easy to read and write - Widely supported | - Relatively large file size - Performance is not as good as binary formats |
| XML | - Powerful query language XPath - Strong scalability | - Large file size - Slow parsing speed |
| CSV | - Simple, easy to generate and parse | - Only supports simple data structures |
| Protobuf | - Efficient, cross-platform | - Requires compilation - Learning curve |
| Avro | - Supports schema evolution, cross-language | - Relatively complex |
| Thrift | - Supports multiple programming languages | - Requires compilation |
| BSON | - Compatible with JSON, more compact | - Requires specific library support |
| YAML | - Easy to write and read | - Performance is not as good as JSON |
| MessagePack | - Smaller and faster than JSON | - Requires specific library support |
| CBOR | - Cross-language, simple schema | - Relatively new, insufficient support |