· Zen HuiFer · Tutorial · 4 min read
Data Alarm Design
This article details the design scheme of data alarms in IoT projects, including temperature monitoring alarms, equipment performance degradation alarms, and multi-device linkage alarms, helping developers better understand and apply data alarm technology.

Data Alarm Design
Scenario Overview
Data alarms are a very important application scenario in IoT projects. In the actual business development process, we may encounter the following possible alarm forms:
- Determine whether the current signal is within a specific range, which can be an alarm within the range or an alarm outside the range.
Example:
Temperature Monitoring Alarm: In an industrial environment, equipment may need to operate within a specific temperature range to ensure efficiency and safety. If the temperature of the equipment exceeds this range, the system will trigger a high-temperature alarm to remind the operator to check the equipment or take cooling measures.
- Alarm within the range: The equipment temperature is normal between 40°C and 60°C. If the equipment temperature continues to be within this range, the system may not issue an alarm.
- Alarm outside the range: If the equipment temperature exceeds 60°C, the system will issue a high-temperature alarm; if it is below 40°C, it may issue a low-temperature alarm.
- Trend comparison, comparing the current data with the previous data to see if it is within a specific range (percentage range). In this mode, it may also be a comparison of multiple historical data rather than just the previous one.
Example:
Equipment Performance Degradation Alarm: During the production process, the performance of the equipment may gradually decline over time. By comparing the current performance indicators with the performance indicators of the previous period, a performance degradation threshold can be set.
- If the performance indicators of the equipment (such as output, speed, etc.) decrease by more than the set percentage (e.g., 5%) for several consecutive periods, the system will issue a performance degradation alarm.
- Multi-device linkage alarm, in this mode, multiple devices will participate in the alarm calculation, and these devices will have a certain correlation in the real scenario. When one of the indicators meets the alarm condition, other device indicators will continue to be observed, and the former is the reference for the latter. If the conditions are met, an alarm will be issued.
Example:
Environmental Monitoring Device Linkage Alarm: In environmental monitoring, different monitoring devices may monitor different parameters of the same environment.
- For example, if an air quality monitoring station in a certain area detects a sudden increase in pollutant concentration, the system will check the meteorological station data in the area to see if there are meteorological conditions that are not conducive to the dispersion of pollutants. If the meteorological conditions are indeed not conducive to dispersion, the system will issue a linkage alarm, indicating that there may be a serious air quality problem.
Engineering Design
In response to the scenarios mentioned above, we have abstractly designed the entire alarm system into two major alarm modes:
- Numerical Alarm
- Script Alarm
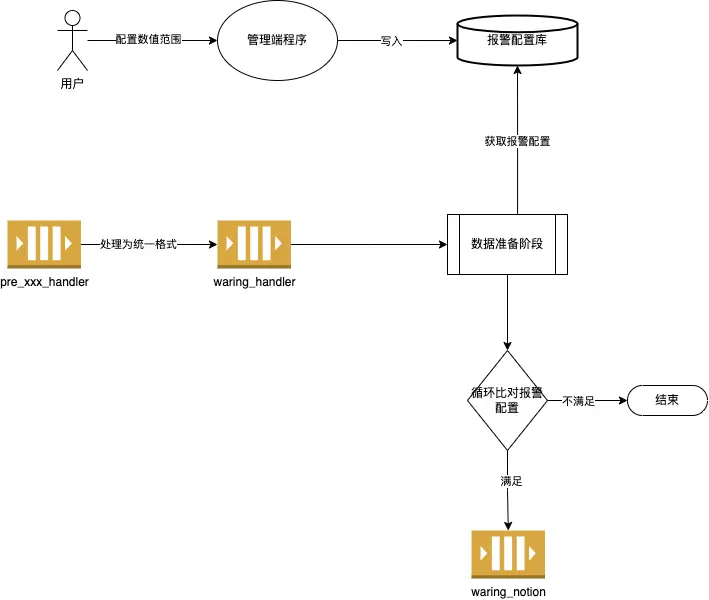
Numerical Alarm
Numerical alarm is a typical scenario of data alarm. Users only need to create signals, threshold ranges, and alarm rules (alarm within the range, alarm outside the range).
Program-side implementation logic: After the device data is parsed, the corresponding data is found in the signal configuration table for numerical comparison. If the threshold condition is met, an alarm is triggered.
Script Alarm
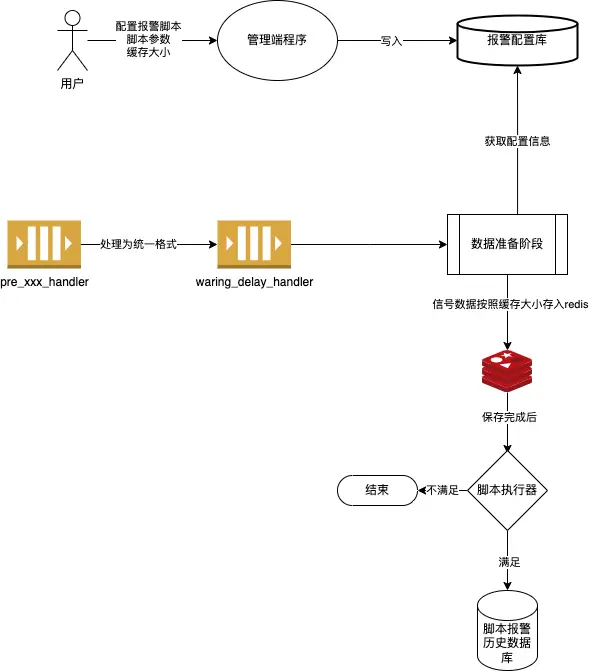
Script alarm is another scenario of data alarm. Users need to create signals, cache size (how many signal historical data to store), alarm script, and script parameters.
The program execution link is as follows:
- After the device data is reported, the data cache is performed. At this time, the cached data has a capacity limit (capacity limit: cache size). The cached data will be used by the subsequent alarm script.
- After the storage of the cached data is completed, the alarm script will be executed. The alarm script is a program written in JavaScript and returns boolean data.